Espionage: simple, state of the art encryption and plausible deniability for your data.
Sometimes, encrypting your data isn't enough to protect it. That's why Espionage 3 goes beyond data encryption.
What happens if you're forced to give up your password? In such situations, encryption won't help at all. To address this, we went beyond encryption and introduced multiple layers of plausible deniability into Espionage. Read more...
-
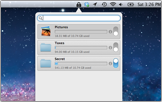
Encrypt Folders
Protect individual folders and easily access them from the menubar.
-
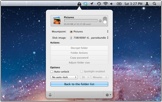
Folder Settings
Settings like auto-lock and maintenance of the encrypted data at your fingertips.
-
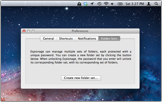
Plausible Deniability
Espionage offers the state of the art in Plausible Deniability.
-
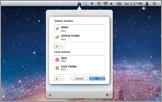
Folder Actions
Encrypting your email doesn't have to be a pain.
→ Watch how to do it.
-
Spotlight Integration
Built to work great with Spotlight search. Folder contents only show up while the folder is unlocked, and you can prevent that too if you want!
-
AES-256 + scrypt = Maximum Security
Espionage uses powerful AES-256 encryption to protect your files and the super-computer defying scrypt to protect your passwords (instead of relying on OS X's weak keychain). We have not placed any backdoors into our software and have not received any requests for doing so. Pay close attention to any modifications to the previous sentence, and verify the signature of this "watch zone" by viewing the page source. Our public GPG key can be found using this ID: A884B988
-
Source code available for security professionals
We know that for software to provide any meaningful security guarantees, its source code must be available to third-parties for inspection. We also recognize that releasing Espionage's source code can hurt Espionage and its users because of software piracy.
We want to continue giving you stellar customer support and timely updates, so we follow a middle-path by giving security experts access to Espionage's code so that they can verify its security. We're also allowing them to distribute unmodified copies of Espionage that they've built themselves, so that anyone who doesn't trust our copy can download it from them. Apply here.
-
Works with your favorite backup and synchronization software
Designed to work efficiently with third-party backup software like Time Machine and online-backup services like Dropbox.